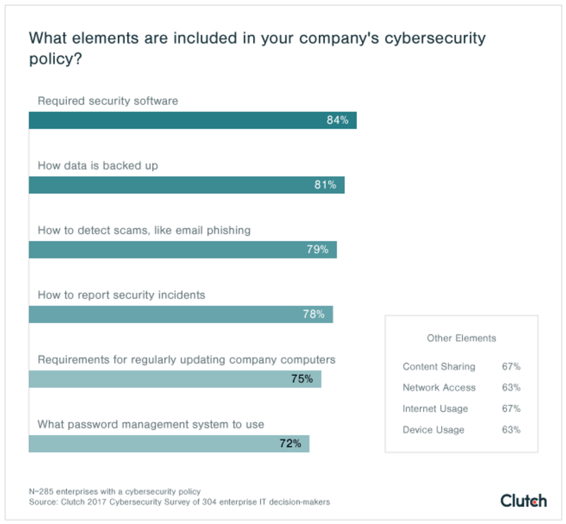
A recent study of large companies by Clutch shows where the cybersecurity focus is for large companies and sheds light into what they're doing about it. Read the Clutch.co study here.
When it comes to looking at cybersecurity from the electronic security perspective, two thoughts rise to the top:
- Can someone get into our electronic security systems, take them down, and execute a physical attack?
- Can someone use electronic security devices to gain access to the rest of our corporate network?
From streaming data to securing equipment racks, we've been covering the 'data security' topic for quite some time.
 We've summarized the information and many of the resources to help you stay on top of this topic:
We've summarized the information and many of the resources to help you stay on top of this topic:
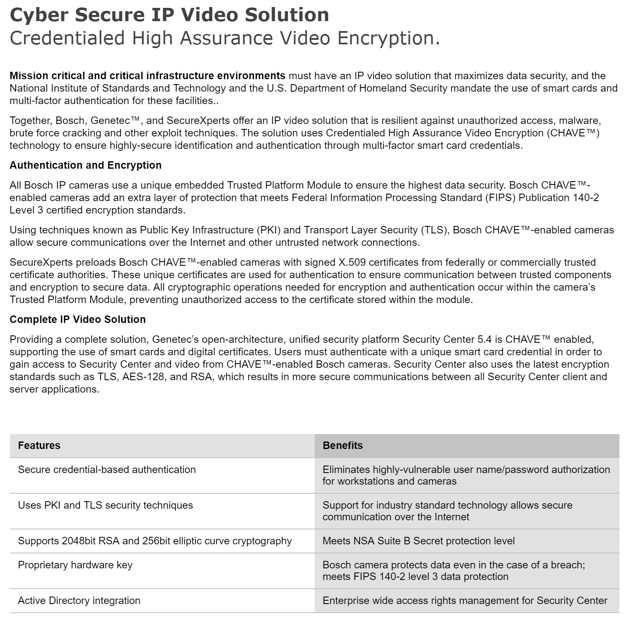
- IP Video and Data Security Guidebook
- Secure the Edge of the Network - White Paper
- 3 Common Security Hacks
- Data Security Leaflet
- Securing Data and Equipment Racks
- Encryption of Intrusion Detection Systems
- Security of Security
- Security Encryption and Certificates FAQ
- PKI CHAVE One-Page
- PKI CHAVE Leaflet
- PKI CHAVE Presentation PPT
- Lessons learned from major health care data breaches
- NIST National Cybersecurity Center of Excellence
- Contact our team for expert security advice