Access management is an essential component of building security. It is the process of granting authorized users the right to enter certain buildings, areas and rooms, while preventing access to non-authorized users. Sounds simple, but today’s market also wants access management systems that are easy to set up and use. Access management systems must also be easily scalable and able to integrate with other security domains like video and intrusion systems. And perhaps most importantly, today’s market wants access management systems that are highly resilient and always available.
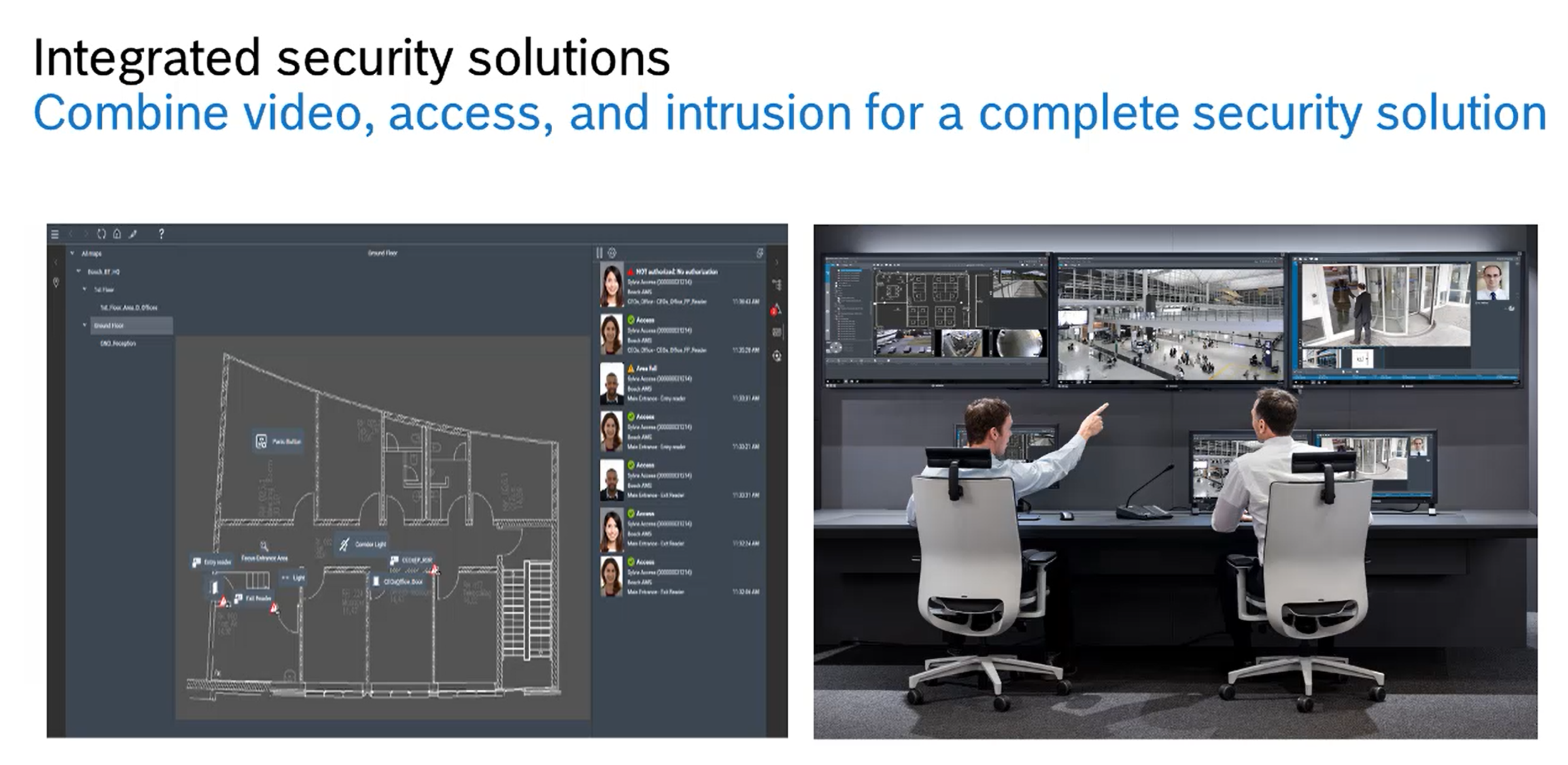
Watch Tom Mechler describe how to effectively leverage video surveillance, access control, and intrusion detection in one unified solution >>
Simplicity throughout

The entire customer journey is designed to be as effortless and as simple as possible. The configuration is easy: existing floor maps are imported into the system and icons are dragged and dropped to represent controllers, doors and building objects on the map view. Onboarding is straightforward: enrolment and assignment of access rights is all implemented in one dialog manager, even the registration of biometric data. The data on several thousand cardholders held in legacy or HR systems can also be quickly imported with just a few clicks, thanks to the importer / exporter tool. The possibility to create access profiles with a certain scope of authorizations makes the assignment of authorizations simple as it is not necessary to assign every single authorization to the cardholder but just one pre-defined role profile. And once set up, using the system is also easy, with an intuitive icon alarm list and color scheme to ensure fast and efficient operator reactions.
Ideal as standalone, capable of growing into a complete security solution

The Access Management System 3.0 is a flexible access management system for medium- to large-sized organizations. It is easy to set up, operate and expand. It offers very high reliability and several features found only in high-end security solutions. The Access Management System 3.0 can grow with the needs of the customer. The software is offered in three pre-configured software bundles for different sized organizations: Lite, Plus and Professional. All three versions are fully functional and can be used directly “out-of-the-box”. They can also be enhanced with further expansion licenses when needed. In total, up to 200,000 cardholders and up to 10,000 doors can be administered. Since no hardware needs replacing, increasing the system size is very cost-efficient. The Access Management System 3.0 can also be integrated with video management systems, and B Series and G Series panels, and it will soon be able to integrate with further Bosch and third party systems. With this integration capability, the Access Management System will serve as the solid platform to mix and match various security systems, depending on the customer’s individual needs. And since it is regularly updated with the latest data security enhancements and because it can easily grow, it is a future-proof investment, ideal for office and governmental buildings, retail environments, educational institutions and hospitals.
Always available

For increased resilience and high availability, the Access Management System 3.0 includes the Master Access Controller (MAC) as an additional layer of resilience between the server and the access controllers. If the server fails in the Access Management System 3.0, the MAC takes over and ensures that the controllers still communicate with each other and share necessary information from the card readers. Thus, even functionalities which include various controllers such as anti-passback, guard tour and area control can still be performed. And to avoid any disruption in the rare event of the workstation and the MAC both failing, a second MAC can be configured as a redundant MAC (R-MAC). This concept provides the customer with the highest system availability.
Integration with video

The Access Management System 3.0 can be integrated with video management systems such as BVMS (10.1 and higher) and Milestone XProtect. Integration with BVMS offers manual video verification to increase the security level at doors. Here the operator verifies if the person at the door matches the registered person in the database and if so allows the person to enter. BVMS integration also enables searching for cardholder events and events at doors. It can be checked which doors and areas have been entered over a specific time by a specific cardholder and which cardholders have entered and left a certain area during a certain period of time. This can be useful when, for example, something is stolen from a certain area. With the searching functionality, it is possible to quickly check who has entered this area and at what time. Moreover, access commands and events can be handled in BVMS, making the operation of the integrated system most efficient.
Integration with B and G Series

B and G Series Intrusion Control Panels integrate seamlessly into the Access Management System 3.0 for efficient authorization management and a central overview of all access and intrusion authorizations. With central user management, operators can add, delete and modify intrusion-related user passcodes and authorizations directly in the Access Management System 3.0, as well as organize users by groups or functionalities. The integrated command and control functionality enables operators to arm and disarm intrusion areas directly in the system's user interface as well as to see their arming status on the system map. This provides operators with a central overview of all access and intrusion states, allowing them to handle intrusion alarms efficiently and remotely.
Threat level management

Up to 15 configurable threat levels mean that safety measures can be initiated quickly in critical situations such as fire or terrorist attack. The threat level state is implemented by one of three triggers: operator workstation, emergency button, or specially configured “emergency” cards that are presented to a reader. The different threat levels can make all doors open, or all doors blocked, or a mix of some open and some blocked. Individual doors can also have their own security profile and allow only certain cardholders access.
Situational awareness

At all times, the operator has full situational awareness thanks to the instant updates of events at the doors via the Swipe Ticker and the comprehensive overview on the on-screen map. The Swipe Ticker provides the operator with a constantly updated list of last cardholders who attempted to gain access to selected doors, it shows who was granted access and who was not. In addition, the map view indicates the respective door on the map to allow the operator to quickly see where exactly the event is happening.
High data security and privacy protection

To protect against cybercrime and loss of personal data, communication is encrypted at all stages. Access Management System 3.0 also has trusted digital certificates for mutual authentication between server and client and uses secure design principles such as “secure-by-default” and
Contact us for system design assistance >>








